True CyberChampion experts are industry veterans, experts with compelling real-life stories to create a relatable context.
Our founder,Beza, has over 15 years of experience crafting, implementing, and evangelizing cybersecurity and privacy protection visions, strategies, programs, and solutions to help businesses and governments achieve cybersecurity and compliance objectives. With his team of experts, he guides organizations to design, deploy and maintain people, processes, and technology effectively to identify risks, protect assets, detect attacks, and respond to and recover from a breach.
Advisory, Assessment, & Monitoring Services
We work with you to assess and understand your organization’s current security risk posture and compliance requirements and craft solutions to develop a risk-based strategic security action plan to mature your cybersecurity programs.
People, Processes, Technology Approach
We believe that cybersecurity is not a technology problem.We empowers your organization with practical solutions to establish a holistic security posture balancing people, processes, and technology.
Average time in days to identify and contain a data breach by Stolen credentials
Average time in days to identify and contain a data breach by business email compromise
Average time in days to identify and contain a data breach by phishing
Average time in days to identify and contain a data breach by third party vulnerability
our services
CYBERSECURITY RISK ADVISORY | AUDIT SUPPORT| FISMA COMPLIANCE | SECURITY TESTING | CYBERSECURITY TRAINING PROGRAMMS |PROGRAM MANAGEMENT
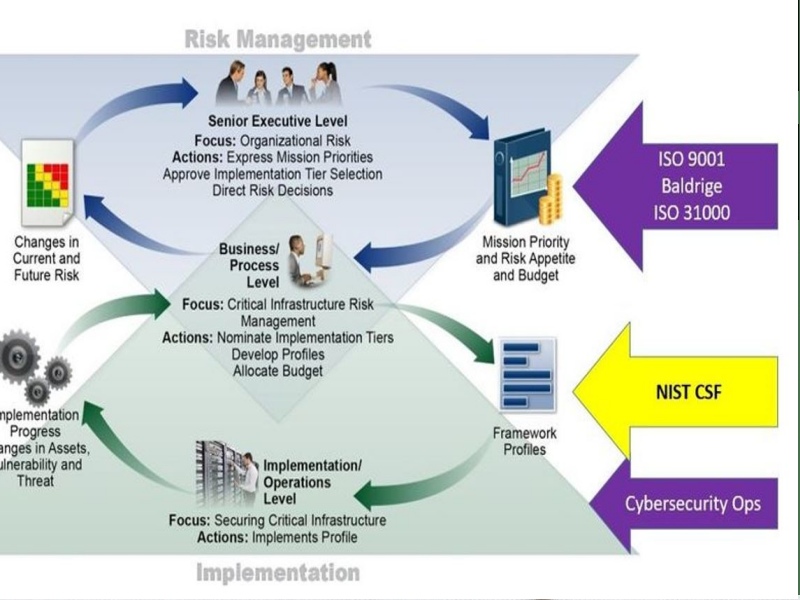
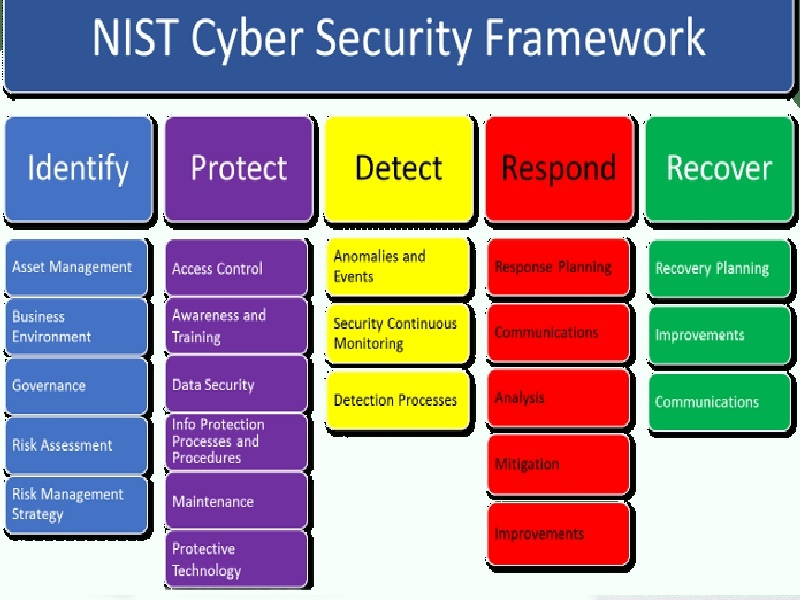
Framework Compliance - FISMA, NIST, CSF
Cybersecurity compliance is a challenge. We can help you win it. We provide cybersecurity strategy and transformation support to achieve the highest level of maturity. Our support will help you build a more secure organization beyond compliance, regardless of where your cybersecurity maturity lies.
Human Error is Responsible for 82% of Data Breaches
According to Verizon’s 2022 Data Breaches Investigation Report, a substatial amount of data breaches involve a human element. Employees’ intentional and unintentional mistakes expose organizations to risks. We have a holistic approach and system to develop robust human-centric processes and training programs.
Cybersecurity Risk Governance & Compliance
Complexity is the enemy of cybersecurity. Overusing cyber jargon, cliches, and scare tactics prevents cybersecurity from gaining executive buy-in and employees’ support. This jeopardizes the security of organization . Our solutions enable you to communicate cybersecurity messages clearly and concisely.
Patching Human Vulnerabilities
Greed and making mistakes are the core of human nature. Add that to cybersecurity fatigue; our adversaries can easily breach the human firewall (It will then be reported as a sophisticated attack). Our actionable strategies help your employees to change Perceptions + Attitudes + Belief = Behavior
Emerging Cybersecurity Threats, Trends, and Solutions
Risks from emerging threats are rising: We would help you develop and implement strategies to mitigate threats from these trends: Social Engineering, Third-Party Exposure, Configuration Mistakes, Poor Cyber Hygiene, Mobile, Cloud, Social, IoT, and poor data management.
Cybersecurity Analytics and Automation
Our Cybersecurity analytics services is a proactive approach to a robust cybersecurity posture by leveraging data collection, aggregation, and analysis capabilities to perform vital security functions that detect, analyze and mitigate cyber threats.
A holistic, end-to-end approach to cybersecurity governance, risk, and compliance
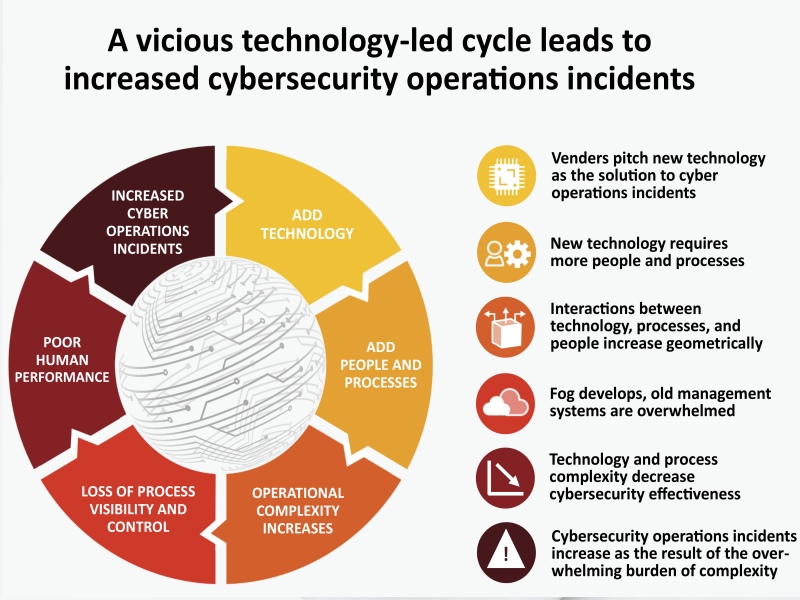
The complexities of managing enterprise cyber initiatives and programs can be overwhelming. The pace of change, the scope of projects, competing priorities, and lack of experienced resources can conspire to stall progress and increase risk. We have extensive experience managing cybersecurity support contracts in the federal government successfully. True CyberChampion can help you understand, prioritize, and address your cyber threats and move forward to mature your cybersecurity programs.
Call To ActionTestimonials
In a world of fake gurus and fake “influencer” mistrust, those who break into cybersecurity have grown weary of inaccurate and unrealistic promises. We appreciate mentors, who are luminaries of the industry, colleagues, partners, and clients, for trusting us to continue providing credible services and leadership to our insecure world.
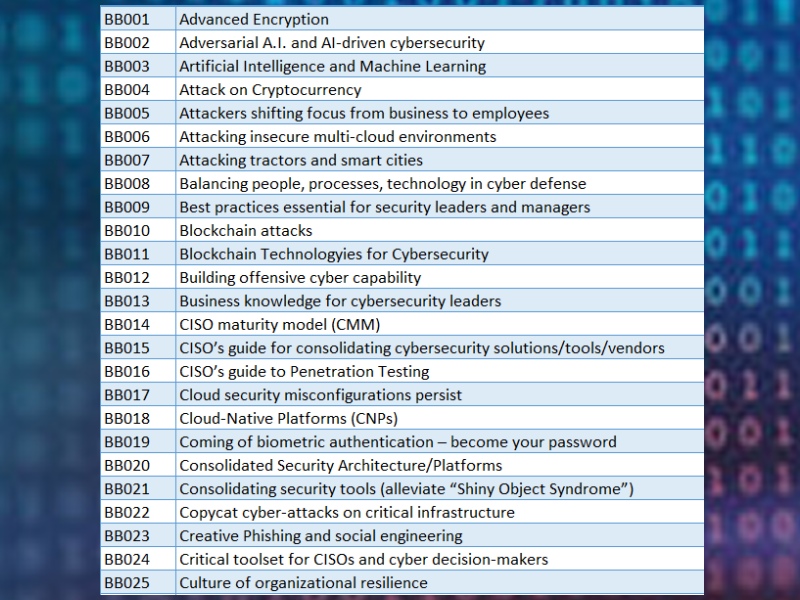
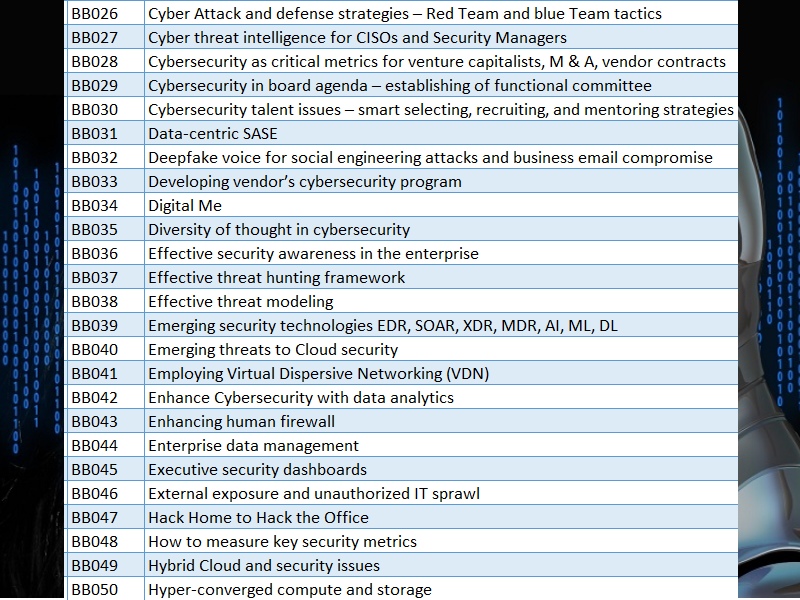
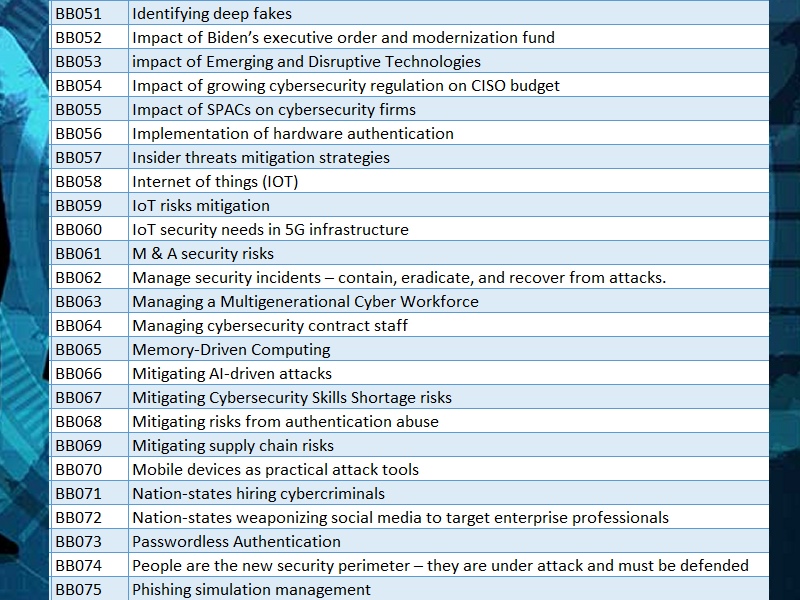
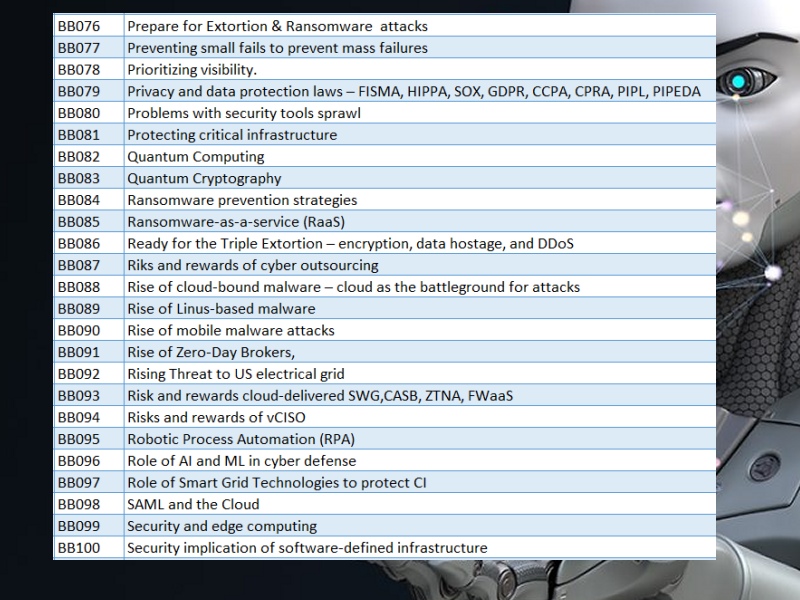
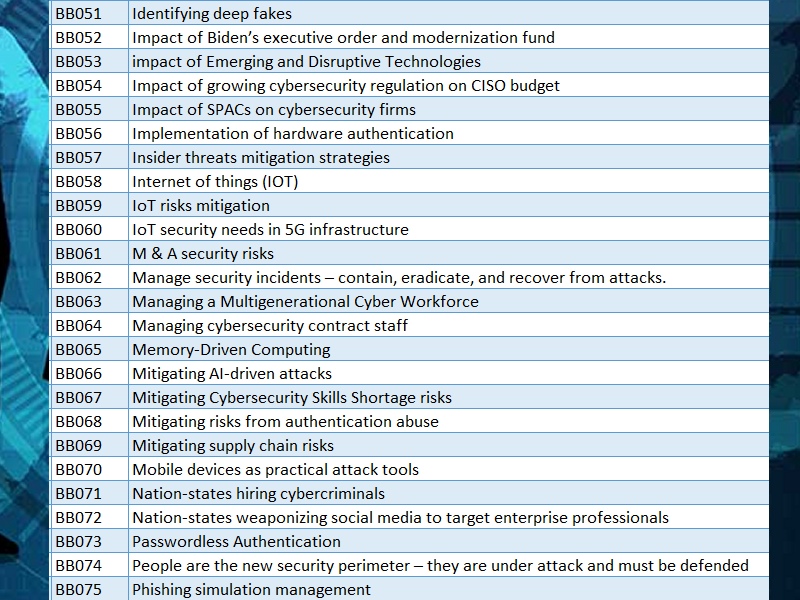
Areas we can provide advisory and training services
Our style of cyber awareness presentations influence human behavior because there is often insufficient attention paid to the" people" equation. There is just no software patch for human error. We believe that reducing the risk of breaches requires changing behavior and reducing the number of opportunities for people to make mistakes. Our training, awareness, and education services will enable cybersecurity programs to be attack-ready and subsequently more successful in preventing and detecting breaches and reduce impacts of data breach.
- All
- People
- Process
- Technology
Frequently Asked Questions
Reach out if you have questions or require to learn how we can transform your cybersecurity capabilities.
-
What first step should we take to use your services?
We seek to understand your business and needs first so we can deliver a personalized approach that adds value. Please send us your request to info@truecyberchampion.com. Contact the federal government POC "beza@truecyberchampion.com" for consultations.
-
How do you deliver cybesecurity training services?
Our training services are customised according to your needs and training sessions are delivered in person or live online
-
Where do we begin the journey towards establishing cybersecurity capabilities ?
The initial action depends on the overall assessement we perform to identify the level of your programs' maturity level.
-
How real are you guys? Can we reach out and talk to human?
We are credentialed professionals with decades of experience in the federal government, education institutions, and the private sector..
-
Where are you guys based?
We are a woman and minority-owned small business proudly operating out of Silver Spring, Maryland, serving the DC metro area..
-
Do you have free initial consultation?
Yes, we offer a consultation call to showcase our capabilities, learn about your needs, and chart the next steps. Our services are offered on flexible and affordable terms.
reach out
Contact us, we will always be happy to provide quick responses for your questions.
Our Address
11393 Columbia Pike, #D10, Silver Spring, MD 20904
Email Us
info"@"TrueCyberChampion.com
Federal Government PoC "Beza"@"TrueCyberChampion.com"
Federal Government PoC Tel #
240 - 476 - 3268
General Enquiries
202 - 699 - 4272